Dams and hydropower facilities have long been attack targets, with a history that spans wartime conflicts. During World War II, the British Royal Air Force formed a group of pilots known as the Dambusters. Their mission: to destroy critical dams in Germany; considered ideal targets due to the significant disruption they could inflict on both water and power supplies.
In 2023 however, the landscape has somewhat shifted. The global cost of cybercrime is projected to soar to $8 trillion. Due to the immense value of data and the potential for widespread disruption, energy and utility companies continue to be prime targets.
Today, the hydropower and dam industries, like many others, stand at a crossroads where innovation and cybersecurity converge. Even a seemingly minor misstep, for instance, untimely dam operations, can unleash havoc upon nearby towns, significantly hampering supply chains and inflicting widespread destruction upon adjacent regions.
Types of cyber threats: State-sponsored and hobby
Cyber threats can be split into two main types. The first is state-sponsored cyber attacks. Those that are planned and funded by governments or nation-states. Kevin Curran, professor of cyber security at Ulster University, recently described cyberattacks by the UK’s enemies as becoming “relentless”. As an example, the Cozy Bear and LockBit hacker groups are believed to be associated with one or more intelligence agencies of Russia, the latter having known links to Russian nationals.
Secondly, hobby-hacker attacks. These hackers are usually motivated by either monetary gain or a wish to cause mischief. One of the most notorious examples is the Colonial Pipeline attack. The company paid the hacker group known as DarkSide 75 bitcoin ($4.4 million) to obtain a decryption key which enabled the company’s IT staff to regain control of its systems.
Growing intricacies of infrastructure create more vulnerabilities
The rising integration of Internet of Things (IoT) devices and sensors within the hydropower and dam sector has brought greater infrastructure complexity, creating more vulnerabilities for several reasons:
- Increasing number of attack surfaces: Every device connected to the network becomes a potential target for attackers. The more IoT devices, sensors and so on that are introduced, the further the range for potential attacks is increased.
- Device security: The substantial volume and often remote location of IoT devices increases the difficulty of keeping firmware and software up-to-date. Moreover, their physical dispersion can expose them to theft and tampering.
- Lack of standardisation: Different manufacturers exercise varying levels of security. The lack of standardisation can make it challenging to implement consistent security practices across all devices.
- Legacy systems: Many critical infrastructure systems still rely on older, legacy technology that may not have been designed with modern cybersecurity standards in mind. These systems are often more vulnerable to attacks.
- Interoperability challenges: Ensuring that different IoT devices and systems work together can be challenging. This can lead to security compromises to enable connectivity, potentially weakening overall security.
- Network visibility: Depending on the network’s connectivity and device location, a 360 view can be difficult to achieve and maintain, making it more difficult to detect and respond to cyber attacks.
- Data privacy: IoT devices often collect and transmit sensitive data. Inadequate data protection measures can lead to data breaches, compromising privacy and potentially providing valuable information to attackers.
The convergence of operation and information technology
Traditionally operational technology (OT) and information technology (IT) data streams remained distinct, which had the benefit of keeping OT systems ‘air gapped’ from the internet, and therefore at limited risk from hacking. As technology unifies OT and IT, it brings both efficiencies and risks. The efficiencies are numerous: by combining SCADA data with the systems that manage physical infrastructure, you can autonomously optimise performance.
But because OT systems haven’t been targets in the past, they’re not always built with security in mind. Passwords are often left at the default character string; remote monitoring for suspicious behaviour hasn’t been implemented; patches are not implemented as frequently as they should be.
In this evolving landscape, it’s critical that security teams are aware of these vulnerabilities and take steps to address them, safeguarding critical infrastructure in the hydropower and dam sector.
Lessons from successful cyber attacks
A successful cyber attack involved Queensland’s Sunwater, a water supplier targeted in a nine-month-long breach. The breach, occurring between August 2020 and May 2021, exploited vulnerabilities in an older system version, granting unauthorised access to customer information stored on their web server. While the hackers didn’t compromise financial or customer data, they left behind suspicious files, redirecting visitor traffic to an online platform.
The subsequent Water 2021 report underscored the importance of immediate action to rectify ongoing security weaknesses, emphasising software updates, stronger passwords, and vigilant network traffic monitoring as crucial safeguards.

In another notable case, the LockerGoga ransomware group inflicted significant damage upon Norsk Hydro. Norsk Hydro was forced to shut down multiple production facilities, impacting 35,000 employees, across 40 countries and resulting in approximately $71 million in financial losses. The cyberattack stemmed from an employee unknowingly opening an infected email three months prior.
Norsk Hydro’s response, however, garnered accolades. The company chose not to pay the ransom, instead engaging with Microsoft’s cybersecurity team to restore operations and remained committed to transparency throughout the ordeal. As Torstein Gimnes, Corporate Information Security Officer emphasised – “You need to rebuild your infrastructure to be safe and be sure that the attacker is not still part of it.”
An immediate IT shutdown was implemented to prevent further spread and only trusted backups facilitated by Microsoft’s team were used. Following the attack, a commitment to employee training, multi-factor authentication, regular updates, and resilient backup solutions were introduced to bolster security.
These cyber attacks underscore the importance of proactive measures and resilience in the face of evolving threats and crucially, they highlight the importance of engaging and sharing knowledge between peers. As Eric Doerr, General Manager of the Microsoft Security Response Center puts it – “When companies do this, it makes us all better and makes the attackers work harder.”
Ensuring the security of critical components in hydropower and dam facilities
Assess cyber risks
- Identify critical assets: Which assets are most important within the facility/network?
- Assess potential risks: What are the potential threats to the identified critical assets? Data breaches, malware attacks, etc.
- Prioritise risks: Which potential risks are more likely to occur and which would have the most significant impact? By prioritising risks, companies can focus resources accordingly.
Mitigate cyber risks
1. Safeguard data
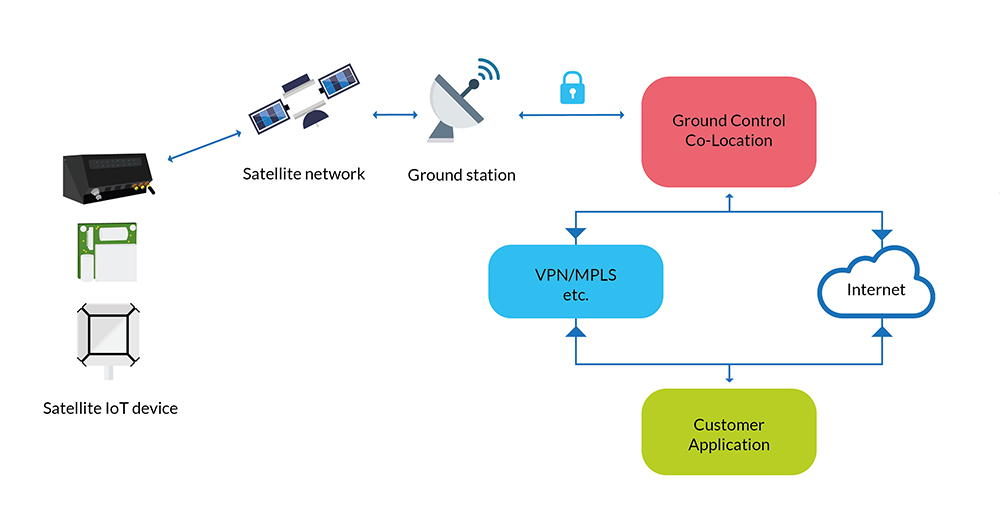
Ensuring data security encompasses data encryption and authentication protocols, coupled with monitoring and restricting physical access to facilities. While firewalls and VPNs serve as effective safeguards when data traverses public internet infrastructure, companies can mitigate these risks entirely with the deployment of private lines or a secure private satellite network like TSAT – designed specifically for SCADA data.
In addition, as mentioned above, recent trends show organisations gravitating toward a unified data stream for both IT and OT. Companies wishing to do this must ensure they have appropriate control system boundary protection to prevent unauthorised access, for example, SD-WAN coupled with a next generation firewall.

2. Secure physical access
Physical security measures not only deter potential threats but also serve as the first line of defence against cyberattacks. By strictly limiting and monitoring who can physically access a facility, organisations can significantly reduce the risk of malicious actors gaining direct entry to sensitive systems and data.
Further, when physical access is under surveillance, companies can identify unauthorised access or unusual activity, allowing them to swiftly intervene and halt a hacker’s progress.
3. Prioritise firmware and software updates
Software and firmware updates are essential tools in addressing known vulnerabilities, strengthening system resilience, and ensuring the integrity of critical software components. By regularly applying updates, organisations stay ahead of cyber threats that often exploit outdated software to breach systems and steal sensitive information.
Firmware updates for hardware devices, on the other hand, enhance device functionality and bolster security by patching potential vulnerabilities. Emphasising the importance of prompt updates and establishing a structured update management process is key. If your dam or hydropower facility is in a remote, unmanned location, ensure that you have the ability to remotely protect your infrastructure with over-the-air (OTA) firmware updates.

4. Staff training
Human errors often open the door to cyber incidents, so it’s crucial organisations equip their employees with the latest cybersecurity knowledge. Early detection and response, facilitated by well-informed and vigilant employees, can prove instrumental in preventing breaches. A prime example is a vigilant staff member who thwarted an attempt to tamper with sodium hydroxide levels in Florida’s water supply last year.
Moreover, robust incident response plans are essential. Employees must know how to contain incidents, restore systems, and investigate root causes. Ultimately organisations need to be confident that if their facility does experience a cyber attack, staff can react efficiently and effectively. Bolstered by continuous training, workshops, webinars, and the cultivation of a security-conscious culture, enhances cybersecurity resilience. It also promotes information sharing among peers, strengthening collective efforts to combat cyber threats.
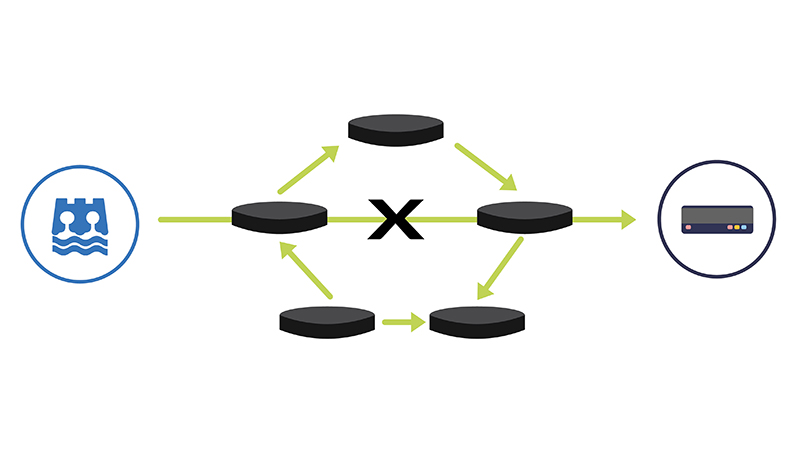
5. Redundancy and backup
Redundancy and backup systems serve as critical safeguards against unforeseen vulnerabilities and disruptions within network infrastructure. By creating duplicate or alternative pathways for data transmission and network operations, redundancy measures ensure that even if a primary system or connection fails, there’s an immediate and seamless switch to a secondary, secure option. This not only mitigates the risk of single points of failure but also enhances the overall reliability of the system.
One of our largest clients has satellite implemented as their third connectivity failover (cellular first, fibre second). Their satellite setup hasn’t failed once in 27 years and is the system they consider the most reliable. With the hydropower and dam sector increasingly reliant on interconnected digital systems, redundancy and backup solutions stand as formidable defences, ensuring continuous operations and protecting against potential cyber threats and disruptions.
The above list is by no means exhaustive, but it does highlight a fundamental truth: In the constantly evolving landscape of cybersecurity, proactive measures are a necessity. Anticipating and addressing vulnerabilities before they become threats is pivotal to achieving and maintaining robust cybersecurity practices. If you would like to explore your connectivity and/or data security options with our experienced team, don’t hesitate to get in touch by emailing hello@groundcontrol.com.
Secure Your Infrastructure
To talk to the team about your connectivity options, challenges and associated data security, simply fill in the form.





