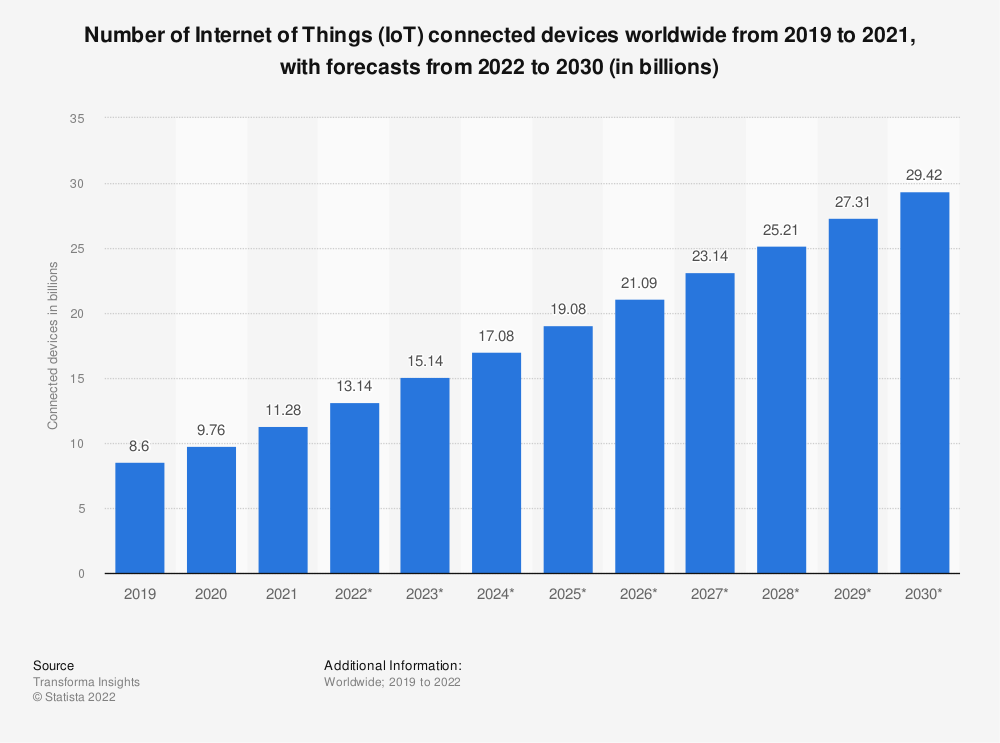
As illustrated in the chart, the global population’s consumer and business appetite for connectivity is getting bigger and shows no signs of abating. Unsurprisingly, this interconnectedness presents an increasingly tempting target for bad actors, whether state-sponsored or not, to disrupt and exploit, as the value of doing so increases exponentially. Indeed, cybercrime is estimated to cost the world $10.5 trillion annually by 2025 (source).
In addition to the explosion in the number of connected devices and users, another security challenge is the push for industrial and network interoperability that increases the movement of data across networks and geological boundaries. All great for business growth and efficiency, but served with an increased number of cyberattack opportunities.
As a result, there’s a growing need to make data security in Industrial IoT a key strategic resilience consideration. And almost no one is sleeping comfortably in the knowledge that their data is completely locked down. In 2022, 96% of surveyed business leaders stated their organisation needed to increase their investment in Industrial security.
If that’s you, let’s unpick some of those potential security threats to Industrial IoT and consider what needs addressing. Also, for those of you already surfing for an eBay ‘build your own bunker’ kit, slow down; let’s start with the good news.
How we benefit from reliable Industrial IoT via satellite
We increasingly rely on IoT for industrial automation and data capture, much of which we can take for granted when effective security measures are in place. Behind the scenes, data transport for Industrial IoT usually travels over cellular or WLAN networks. However, outside of cellular coverage, data can be backhauled via a satellite network. Iridium and Viasat are just two reputable, well-established networks in a growing marketplace of satellite network providers, delivering reliable global coverage and WLAN/cellular failover.
Satellite connectivity can provide access to, and maintenance of, remote IoT devices. The connectivity for tracking and monitoring keeps data flowing and people, equipment, vehicles, and machinery, safe and in check, even in the most remote, off-grid locations. There is a lot to celebrate in the fast-growing world of Industrial Satellite IoT (and if you’re interested to read more about some innovative Industrial IoT Satellite use cases take a look here).
But satellite IoT connectivity is not immune to security challenges. So, for those of you still peeping out from that bunker…
What are the satellite Industrial IoT security risks?
With satellite network security, breach risks can occur at a service provider or data centre level. These earthbound entry points have the potential for satellite network jamming, unauthorised network access, disrupted communications, account or data interception, and the loss of sensitive information.
Risk comes too in the form of device damage – industrial equipment or IoT device sabotage has serious implications for operational technology, production, and manufacturing.
“IoT devices are now the number one attack target on the Internet” – F5 Labs’ The Hunt for IoT
If your device is remote out at sea or in the middle of the Antarctic it’s unlikely that it’s facing a significant vandalism risk (it will need to be hardy though, and able to handle the storm!). Regardless of location, Industrial IoT devices are potential entry points for bad actors hacking into your data or the network.
If you’re thinking, ‘we’re only a small business, we’re not a target’, think again. The 2021 IBM data breach report states the average data breach cost to small businesses increased from $2.35 million in 2020 to $2.98 million in 2021, a 26.8% increase. The risks are a serious matter whatever the size of your operation.
How might these risks be mitigated?
1. Security strategy and risk assessment
In addition to a thorough risk assessment of your IoT network, consider embedding a ‘zero trust, validate first’ employee mindset. This isn’t without challenges; the more agile the organisation, the higher the propensity for risk-taking and the potential for vulnerability and attack. Too much hypervigilance and consequence, and you can quash the initiative and innate talents of the workforce.
The Lloyd’s Register Foundation ‘Foresight review‘ explores this in the unique challenges of maritime IoT: engineers on ships that are used to a high degree of independence, and “solving problems with a wrench and duct tape”. While unquestionably talented, they don’t necessarily have a security mindset, and have been known to “optimise” a network for speed by installing a patch that removes security segregation, for example. The challenge is further compounded because ships can pick up spare parts and new crew anywhere in the world.
But the reality is that the speed of change within IIoT is matched by an equal momentum for malicious activity, and the greatest risk is that some form of human error will let them in. If you assume a breach is inevitable, there can be a competitive advantage in resilience planning, speedy recovery, and shutting down the extent of damage reached within the organisation, or at a minimum, containing the losses.
2. Determine the boundaries of your cyber-security accountability
Think about the interconnectedness of your business and the inter-dependencies within your supply chain. Where there is interdependence there is often complexity, unclear ownership of the risks, and ambiguity about the resolve or culpability. It’s important to have these difficult conversations upfront, and the ownership clarified (be it shared or clearly defined) before there is a breach, rather than trying to unpick any accountability after the damage has been done.
This useful article from Ground Control’s partner Thales outlines the global regulation of IoT. It provides clarity on regulation compliance and mandatory actions that legally govern Europe/UK and the US to ensure connected devices are more resilient to threat and attack and the key data is protected. It also points out evolving consequences for parties not taking accountability.
Ground Control holds ISO 27001 and Cyber Essentials certifications, international standards which help businesses to protect their data and programs from cyber attacks. Holding certification evidences investment into processes and behaviours that offer credibility and trust both to customers, and other companies seeking to partner in an IIoT solution development.
3. Select a security-focused satellite network
No satellite network operator (i.e. the companies who own the satellites and ground stations) is cavalier with data; by default, satellite data traffic is already relatively secure, and meets most military and government security standards. However, having robust network access control further mitigates the risks; this relates to the transfer of data from the ground stations to customers’ servers.
Ground Control has our own custom-built delivery network for Iridium and Inmarsat traffic; this allows us to have full control over our certified, cutting-edge data paths while securely delivering traffic. We built this because we wanted to deliver additional security for our customers’ data, and offer optional public static IPs and completely configurable firewalls to assist in securely moving your data from A to B.
Ground Control’s network offers tiered options around data security which comes down to a choice of monetary investment and required autonomy:
- Mid Level: Data can be encrypted by the customer and sent over a satellite link before decrypting once landed. A VPN (Virtual Private Network) can also be established over the satellite link (though this adds latency and overheads).
- High Level: Ground Control can also set up a VPN from our data centre directly to a customer’s server; this creates a secure virtual tunnel between these two points, preventing access from anyone outside the VPN. A private VPN set-up can save costs as public static IPs are no longer required.
- Highest Level: Set up of an attributed Private Network – Ground Control’s TSAT service offers a completely private and secure network with customers given their own dedicated frequency on the space segment. This is an extremely secure solution with relatively low OPEX costs.
For Viasat and Iridium traffic, Ground Control is also able to discuss installing an MPLS (Multi Protocol Label Switching) or Leased-Line offering a private network solution.
We recommend checking with your network operator to understand the precautions that they are taking to ensure your data is protected. If you want to know how satellite network operators Iridium and Inmarsat keep the data they handle safe and secure, you can read more here:
- Iridium – https://www.iridium.com/markets/defense-intelligence-national-security/
- Viasat – https://www.viasat.com/government/security/cybersecurity/
If you’re interested in reading more about managing your own network securely, take a look at our blog on network security measures.
4. Protect access to your data
In satellite IoT devices, encryption can be used to protect sensitive data that is transmitted between the device and the satellite network. With Ground Control, Short Burst Data (SBD) payloads can optionally be AES-256 encrypted. This encryption increases the data volume by 16 bytes for every transmission (due to the need to transmit an initialisation vector), and therefore incrementally the network costs for data transfer are slightly more. Rates will vary according to the network you are using, so it’s something to be aware of when establishing data transfer costs.
Data encryption combined with satellite network activity (large, continually changing Doppler shifts, frequent inter-beam and inter-SV handoffs, TDMA burst mode channels, and complex modulation, interleaving, and encoding) limits the opportunities to eavesdrop on the satellite communication.
In addition to encryption, selecting security protocols such as SSL/TLS, IPSec, and DTLS provide a layer of security that can help to protect data in transit from interception and tampering.
On the local network architecture, segmenting assets and implementing deliberate fire-breaks to reduce the blast radius of any successful cyber attack, and backing up critical system data are IIoT infrastructure design considerations. Routine monitoring of connections, knowing your employee and site routine network activity and rhythms in order to spot anomalies, checking for behaviour patterns, and investigating when routines are broken or new unrecognised connections are made, go some way to reducing risks and system infiltration.
5. Keep device(s) protected
When selecting satellite hardware or components, prioritise those designed with inbuilt security that meets industry standards. This might include hardware with encryption capabilities, secure boot processes, and built-in security features such as firewalls.
Devices like the RockREMOTE Rugged, which contains an encryption feature set on the operating system that when activated protects data travelling to and from the satellite or cellular network. Consider also purchasing devices that are compact and discreet, drawing less attention wherever they or accompanying antennae are positioned.
It’s equally important to understand the vulnerabilities of any end-point devices such as sensors, cameras, and their underlying hardware and software. These can become vulnerable to attack if the components are outdated, the software is unpatched, they hold insecure default settings, or are under-protected connections to the network.
In the monitoring of the behaviour of devices on the network, access controls can help to prevent unauthorised activity. Access to the device’s firmware, configuration, and other sensitive information should be controlled and monitored. This includes using strong passwords, multi-factor authentication, and limiting access to only authorised personnel.
We’d recommend a configuration management process to ensure that changes to the device’s settings or firmware are authorised and properly documented and regular assessment for vulnerabilities, patches. If this can be automated or handled remotely this makes for operational efficiency. Regularly updating and patching systems can address known security vulnerabilities and reduce the risk of cyber attack.
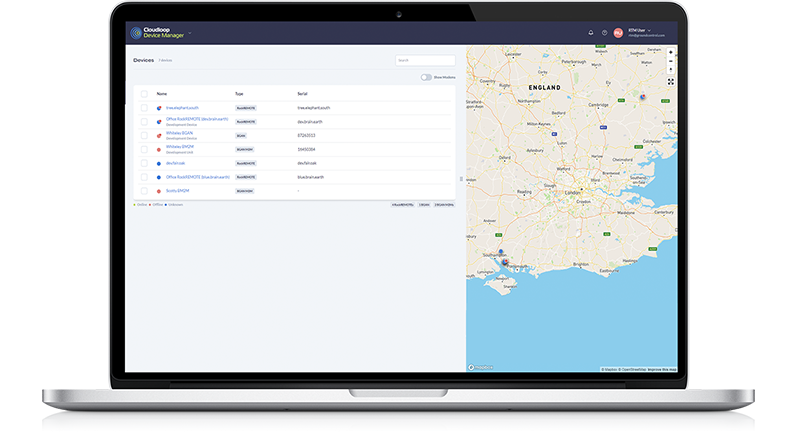
Ground Control makes this easy for customers with Cloudloop Device Manager (CDM), a function within the Cloudloop ecosystem (which also provides subscription and data management tools).
CDM enables customers to remotely access, monitor, troubleshoot, and manage the functionality of their device(s), including device firmware, and patch updates, monitoring usage, and connection.
It gives real-time visibility to issues with devices deployed in hard-to-reach, or physically dangerous locations. It’s simple to use via laptop or any other connected device for access, and from the comfort of home, bunker, or office, Cloudloop provides ease and peace of mind.
One of the noticeable trends in the field of cyber-security is the pace and rate of change. Keeping up with this can be difficult. Securing IIoT infrastructure can be a challenging task for companies and finding the right expertise to support your ambitions can be difficult.
Talk to an expert
Complete the online form, or call or email us, and we'll be happy to provide impartial, expert advice on satellite IoT security as it relates to your application.